AiTM Phishing Page
The primary stage of the phishing attack is the Adversary-in-the-Middle (AiTM) phishing page.
At this stage, the attacker hosts AiTM infrastructure that sits between the user and the legitimate website, acting as a proxy during the authentication process. This allows the attacker to relay traffic while observing the interaction. Learn More
There are two kinds of AiTM phishing infrastructure:
Direct proxy
Indirect proxy
In some cases, attackers also deploy additional infrastructure to relay information between the AiTM proxy and the legitimate service.
More details on these approaches are outlined below.
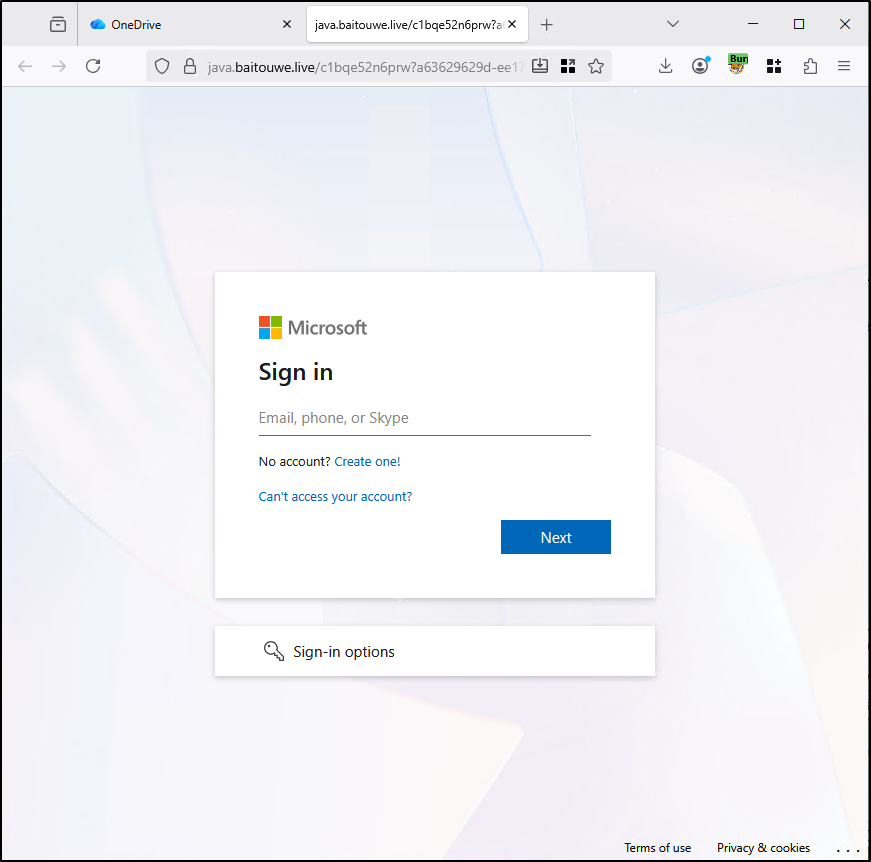
Example
Direct Proxy
In this type of AiTM attack, the attacker's infrastructure seamlessly proxies data between the victim and the real website, without modifying the data that goes between them.
Indirect Proxy
In this type of AiTM attack, the attacker's AiTM infrastructure either manipulates the data that goes between the victim and the real website, or hosts a website to mimic the real webpage, but uses AiTM infrastructure to proxy the backend data between the victim and the real website.
Additional Relay Server
In some cases, the attacker utilizes an additional server that goes between its AiTM infrastructure and the real website. Attackers can cycle between proxies, compromised IOT devices or other compromised infrastructure so the real website sees connections from locations that may not be flagged as high-risk.